Introduction
In moment’s digital-first world, startups and small brigades calculate heavily on cloud platforms to store data, run operations, and unite seamlessly. The cloud offers inflexibility, scalability, and cost- effectiveness — rates that are especially precious for youthful businesses trying to grow presto without breaking the bank.
But with great convenience comes great responsibility. Every train uploaded, every tool connected, and every login credential stored in the cloud can become an implicit security threat if not duly managed. Unlike large enterprises, startups frequently warrant big IT departments or huge budgets for cybersecurity. That’s why understanding and applying all security stylish practices is pivotal not just to cover sensitive data, but also to make trust with guests and mates.
So, let’s break down what cloud security really means, the pitfalls involved, and the practices every platoon or incipient should follow to stay safe in the Cloud.
Why Cloud Security Matters
Cloud computing has converted how businesses operate. Rather than maintaining precious waiters and structure, brigades can now pay for cloud services as they grow. But this ease of use also opens doors for cybercriminals.
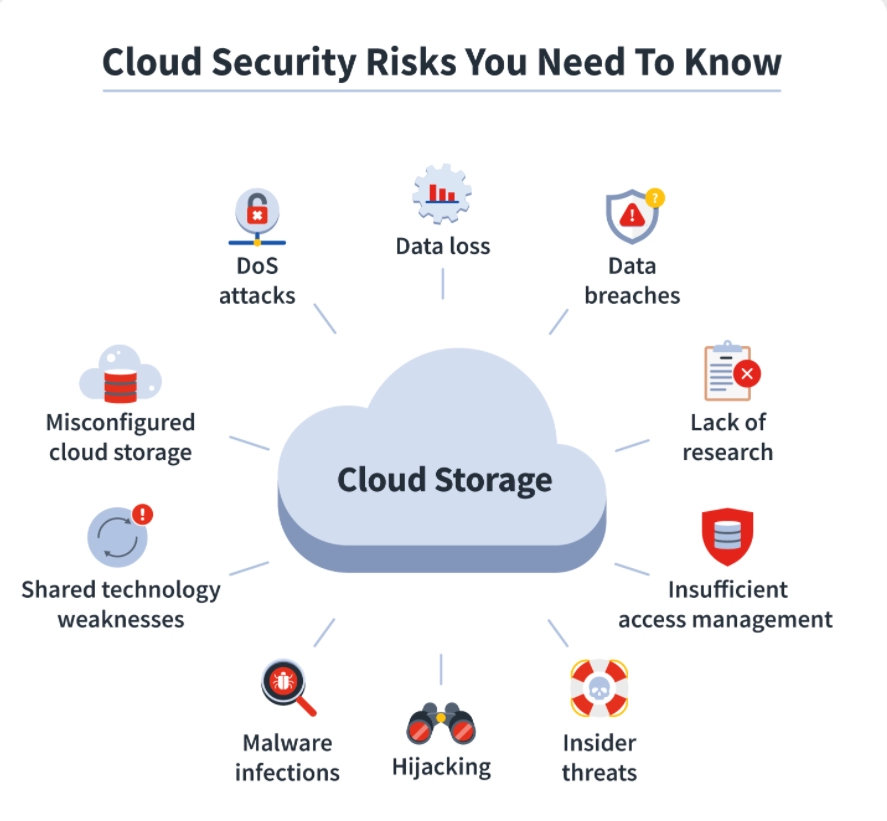
Some of the most common pitfalls in all surroundings include
- Data breaches – Hackers stealing client or business data.
- Account kidnapping – Compromised login credentials used to pierce systems.
- Bigwig pitfalls – workers or contractors misusing access, designedly or unintentionally.
- Miss configurations – A simple error, like leaving a storehouse pail public, can expose sensitive lines.
- Ransomware attacks – vicious actors cracking cloud data and demanding payment for its release.
For startups, indeed a single incident can beget ruinous damage — loss of guests, fiscal penalties, and reputational detriment. That’s why getting cloud security right from the launch is non-negotiable.
Cloud Security Best Practices for Teams and Startups
Now that we understand the pitfalls, let’s look at the way startups and small brigades can take to secure their cloud surroundings.
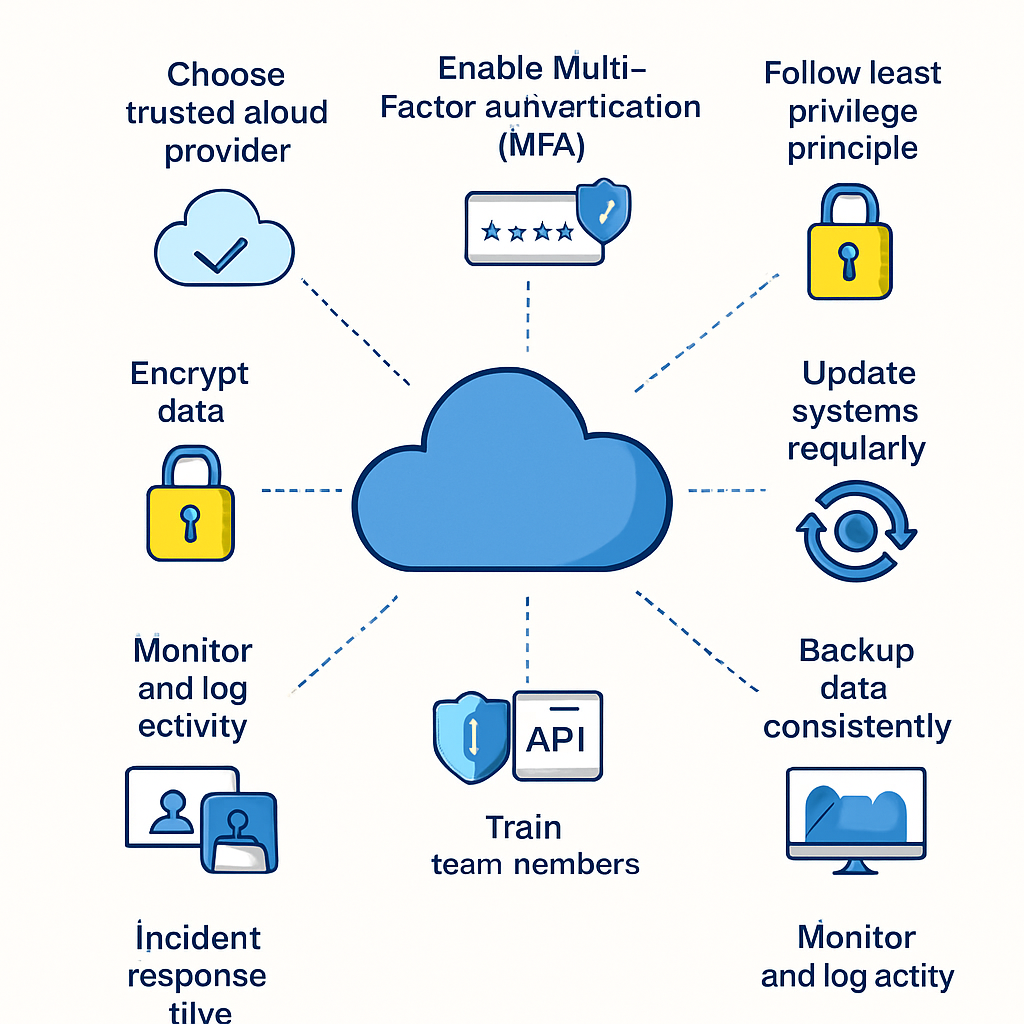
1. Choose a Trusted pall Provider
The first step to cloud security is opting the right provider. Whether it’s AWS, Google Cloud, Microsoft Azure, or another service, make the provider has
- Strong compliance certificate( like ISO, SOC 2, GDPR, or HIPAA, if useful).
- Erected- in security features like encryption, identity operation, and monitoring tools.
- Transparent programs about data power and insulation.
Do some disquisition and pick a platform that not only fits your technical conditions but also takes security seriously.
2. Enable Multi-Factor Authentication( MFA)
Passwords alone are no longer enough. Startups frequently make the mistake of counting on simple logins, which bushwhackers can fluently compromise. Enabling multi-factor authentication ( like SMS canons, authenticator apps, or biometric checks) adds a redundant subcaste of security. Indeed if a hacker gets a word, they still need the alternate factor to gain access.
3. Follow the Principle of Least honor( PoLP)
Not every team member needs access to everything. Give workers only the warrants they need to perform their places. For illustration, a marketing intern does not need access to fiscal databases. By limiting warrants, you reduce the damage that could be if an account is compromised.
4. Encrypt Data at Rest and in Transit
Data should always be defended, whether it’s sitting in the cloud or moving between waiters. At most cloud l providers offer encryption tools to make sure they’re enabled. Encryption ensures that even if data is stolen, it can’t be read without the correct keys.
5. Regularly Update and Patch Systems
Cyber bushwhackers often target outdated software and unpatched vulnerabilities. Set up a schedule to regularly operate, operating systems, and third- party tools. Multitudinous cloud providers allow automated updates — turn this point on whenever possible.
6. Provisory Your Data constantly
Imagine losing your entire client database overnight. That’s the reality for startups hit with ransomware or accidental elisions. Always back up your data — rather in multiple locales.Cloud providers frequently include automated backup features; use them and regularly test that backups can be restored.
7. Examiner and Log exertion
Visibility is crucial. Enable logging and covering in your pall terrain to track who’s penetrating what, when, and from where. Numerous providers offer dashboards that warn you of suspicious conditioning, like logins from unusual locales or unauthorized train downloads. Beforehand discovery can help small issues from getting big disasters.
8. Train Your Team on Security Awareness
Technology alone ca not stop mortal error. Phishing emails, weak watchwords, and careless sharing of links are still among the top causes of pall breaches. Educate your platoon about:
- Feting phishing attempts.
- Creating strong, unique watchwords.
- The significance of reporting suspicious exertion incontinently.
Security mindfulness should be part of your incipiency’s culture, not just an afterthought.
9. Secure APIs and Third- Party Integrations
Startups frequently use multiple tools that integrate with the pall — CRMs, payment processors, analytics software, etc. Each integration can be an implicit entry point for bushwhackers. Use secure APIs, limit what data is participated, and regularly inspect which third- party apps have access to your systems.
10. Plan for Incident Response
No system is 100 secure. What matters is how set you’re when a commodity goes wrong. produce a simple incident response plan that outlines
- Who to communicate in case of a breach.
- Steps to insulate and contain the issue.
- Communication procedures with guests, mates, and controllers.
Even a small incipiency should have a playbook for dealing with extremities — it could save precious time and coffers.
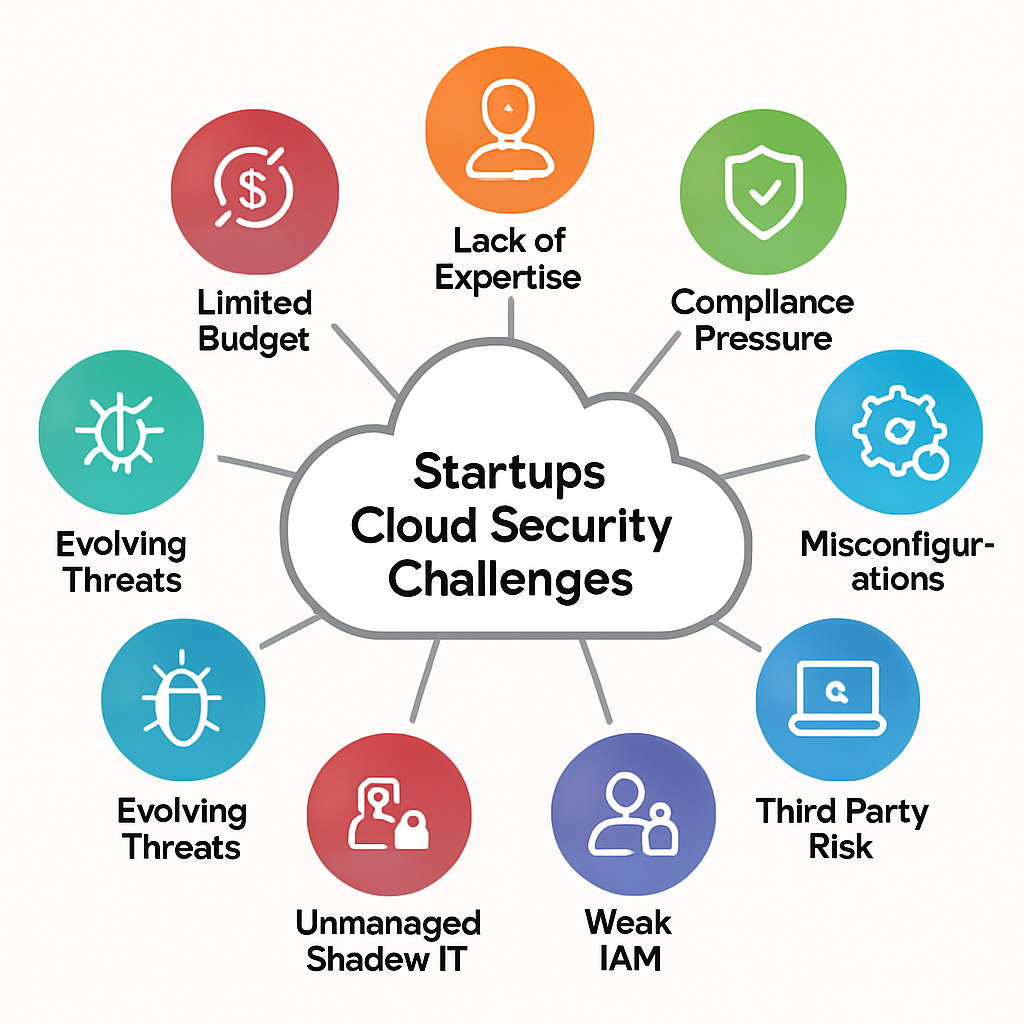
Cloud Security Challenges Unique to Startups
Startups encounter specific difficulties when it comes to securing their cloud surroundings
- Limited resources – frequently, the budget allocated for security is small, which means precisely choosing where to concentrate sweats is essential.
- Rapid growth – As startups expand, they snappily add new tools and platoon members, which can raise the chances of security pitfalls.
- Lack of expertise – numerous startups can not go to a devoted security platoon, so they frequently depend on the erected- in security features handed out by cloud service providers.
The result is to begin with straightforward, high- impact security practices similar as multi-factor authentication, regular data backups, and strict access control.
As the company grows, these practices can be expanded into a further comprehensive security frame.
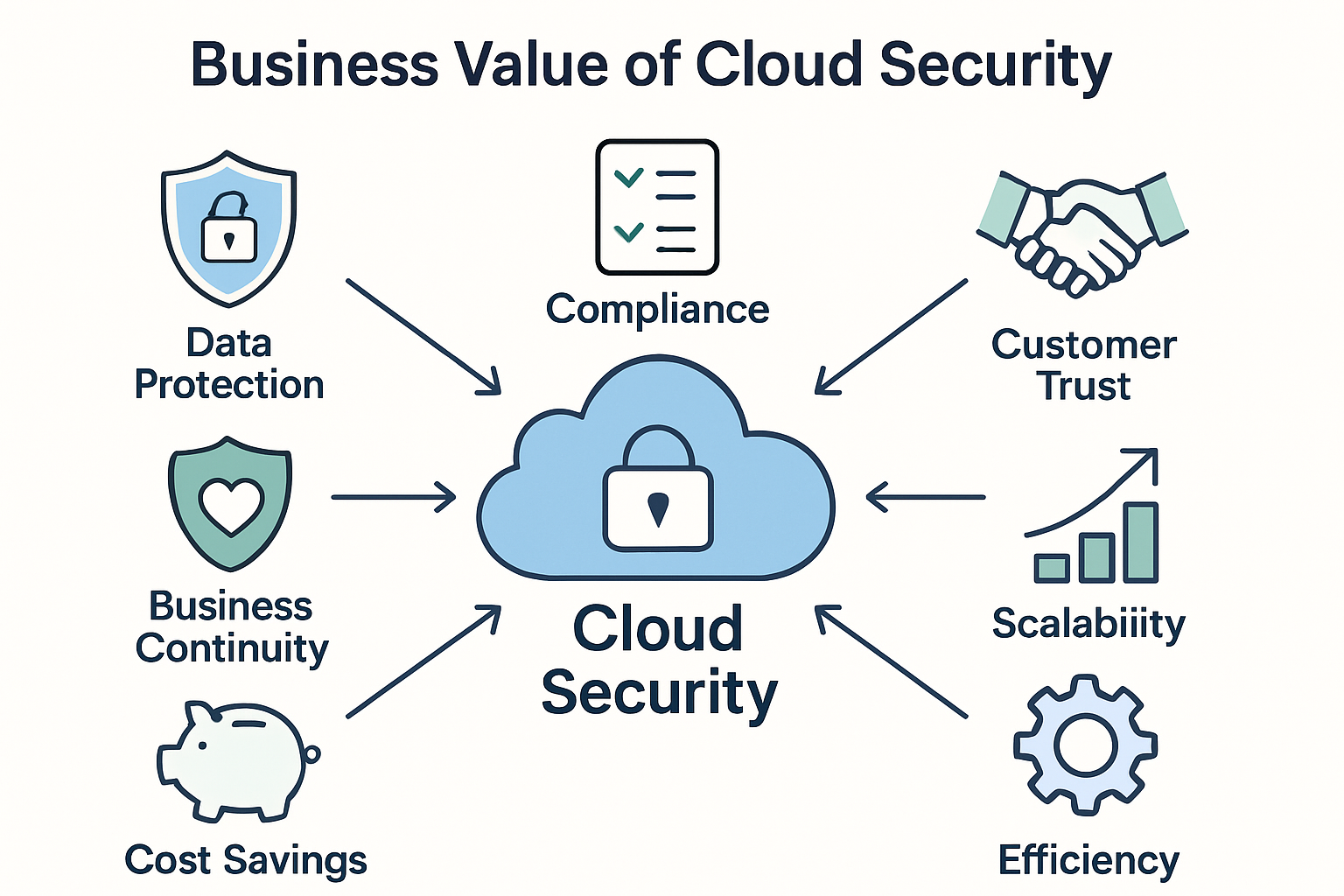
The Business Value of Cloud Security
Effective cloud security is further than just precluding cyberattacks; it also helps in erecting trust.
Guests, investors, and business mates anticipate to know that their information is safe when they engage with your incipiency. For startups, a strong security posture can actually give a competitive edge.
When an incipiency demonstrates a serious approach to data protection, it shows professionalism, trustability, and responsibility.These rates help support the incipiency’s character and make it stand out in a competitive request.
Conclusion
For startups and their brigades, the pall is an important resource but also a possible threat.
Indeed though startups may not have the fiscal coffers of large enterprises, they can still cover their cloud environment by enforcing stylish practices similar to enabling multi-factor authentication, cracking data, training workers, and preparing for security incidents.
Keep in mind that security isn’t a commodity that can be set up formally and forgotten.
It requires nonstop attention and enhancement. The earlier your incipiency makes cloud security a precedence, the more stable and strong your foundation will be as you grow.