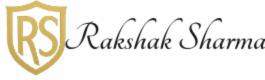What is Phishing?
Phishing is a type of social engineering attack and online fraud in which cyber criminals trick individuals into participating in nonpublic information or intentionally installing vicious software similar as ransomware, adware, worms, or contagions. Over the times, phishing styles have come more advanced, frequently creating websites that look identical to genuine bones . This allows bushwhackers to cover every action the victim takes, bypassing security checks while appearing licit. According to the FBI’s Internet Crime Complaint Center, phishing has remained the most reported cybercrime since 2020.
Ultra modern Phishing Tactics
The phishing moment goes beyond stealing just usernames and watchwords. numerous juggernauts now target multi-factor authentication( MFA) systems. bushwhackers make fake login doors and use relay tools to capture not only credentials but also one- time passcodes. Some phishing accoutrements indeed forward this information in real- time, giving hackers instant access. In 2024, Microsoft Entra stressed the rise of adversary- in- the- middle( AiTM) phishing, where culprits block authentication commemoratives, allowing them to log in as the victim despite MFA protections.
Origin of the Term Phishing
The word phishing dates back to themid-1990s. It first appeared in the hacking toolkit AOHell( 1995), although some substantiation suggests it may have been used before in the hacker magazine 2600. The name is deduced from “ fishing, ” emblematizing how bushwhackers use fake lures to “ hook ” sensitive data from unknowing druggies.
Combating Phishing
Reducing the risks of phishing requires a combination of strategies. Governments calculate laws and regulations, while associations concentrate on security awareness training and public campaigns. Specialized defenses, similar to dispatch- malware tools, and strong authentication systems, also play a vital part. The need for phishing awareness is rising swiftly — in businesses, reported cases grew from 72 in 2017 to 86 in 2020, and further increased to 94 by 2023.

Types of Phishing
Phishing comes in numerous forms, depending on how bushwhackers trick people. Below are the most common types:
1. Email Phishing
- The most common form.
- bushwhackers shoot fake emails pretending to be from trusted companies( banks, shopping spots, or government services).
- These emails generally contain vicious links or attachments that steal information once clicked.
2. Spear Phishing
- A targeted attack aimed at a specific individual or association.
- Rather than transferring mass emails, bushwhackers probe the victim’s job, interests, or connections to make the communication more satisfying.
- illustration An dispatch that looks like it came from your master asking for nonpublic lines.
3. Whaling
- A special type of shaft phishing that targets high- profile people, similar to CEOs, directors, or government officers.
- Since the “ big fish ”( jumbos) hold precious data or authority, bushwhackers craft largely satisfying dispatches to trick them.
4. Smishing (SMS Phishing)
- Phishing carried out through text messages (SMS).
- Victims receive a message claiming to be from a bank or courier service, with a link that steals information.
- Example: “Your account is locked. Click here to verify.”
5. Vishing (Voice Phishing)
- bushwhackers make phone calls pretending to be client support, bank officers, or government representatives.
- They produce urgency( like “ your account will be blocked ”) and pressure the victim to reveal sensitive details.
6. Clone Phishing
- A genuine email you once received is cloned and resent with a malicious link or attachment.
- Since it looks familiar, victims often fall for it.
7. Pharming
- Rather than tricking the stoner, bushwhackers manipulate website business.
- Indeed if you class the correct website address, you may be diverted to a fake point that looks identical to the real bone .
8. Angler Phishing (Social Media Phishing)
- Done on social media platforms using fake customer support accounts, ads, or messages.
- Example: A fake account replying to your complaint tweet with a vicious link to “ fix ” your problem
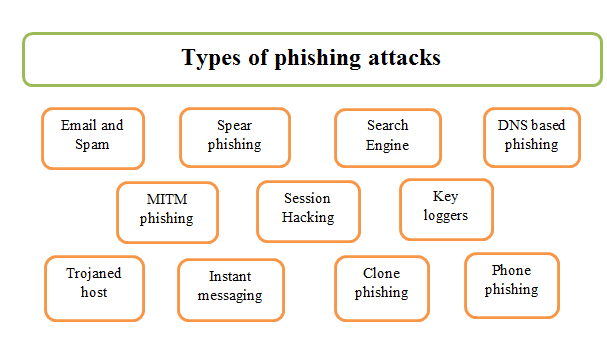
Techniques
Phishing is one of the most common cyber pitfalls, and bushwhackers use a variety of ways to deceive druggies. These ways exploit mortal psychology, trust, and digital vulnerabilities to steal sensitive information similar as watchwords, fiscal details, and particular data. In below some are the common ways of phishing-
1. Deceptive Emails
The most extensively used phishing system involves transferring fraudulent emails that appear to come from trusted associations like banks, shopping websites, or government agencies. These emails frequently produce a sense of urgency, similar as advising about account suspense, to press druggies into clicking on vicious links.
2. Fake Websites (Spoofing)
Phishers design websites that look identical to licit bones . Victims are diverted to these caricatured login runners, where they intentionally enter their credentials, which are also stolen.
3. Spear Phishing
Unlike mass phishing, shaft phishing targets specific individualities or associations Attackers use personal or professional information to make the message appear more genuine, increasing the chances of success.
4. Whaling
A technical shaft phishing attack that targets high- profile individuals similar to CEOs, directors, or government officers. These attacks are precisely drafted and frequently aim to steal large quantities of sensitive data.
5. Smishing and Vishing
- Smishing transferring fake dispatches via SMS/ textbooks to trick druggies into clicking links or participating data.
- Vishing Voice phishing is done through phone calls, where bushwhackers impersonate officers or client service representatives.
6. Clone Phishing
bushwhackers take a licit dispatch preliminarily entered by the victim, copy it, and resend it with vicious links or attachments. Since the dispatch looks familiar, the victim is more likely to trust it.
7. Pharming
Rather than tricking the stoner directly, bushwhackers manipulate DNS settings or use malware to deflect drugs from a licit website to a fraudulent one, indeed when the correct web address is entered..
8. Adversary-in-the-Middle (AiTM)
A modern phishing method where attackers intercept communications between a user and a website. By capturing login credentials and authentication tokens in real time, they can bypass even multi-factor authentication (MFA).
History of Phishing

Early History (1990s)
Phishing ways first appeared in themid-1990s, when hackers in the warez community exploited AOL druggies. Tools like AOHell( 1994) allowed bushwhackers to impersonate AOL staff and trick druggies into revealing their login details and credit card figures. This marked the birth of phishing as a form of online fraud, forcing AOL to strengthen its defenses and shut down large- scale swindles.
2000s – Rise of Organized Phishing

The 2010s saw phishing attacks evolve into global, largely targeted juggernauts. In 2011, RSA’s SecurID commemoratives were compromised via phishing. By 2013, retail giant Target lost 110 million records due to a subcontractor phishing breach. Fancy Bear, a Russian hacking group, conducted shaft- phishing juggernauts against NATO, the White House, and the Democratic National Committee( 2016). pall services and social networks came top targets, with incidents like the iCloud celebrity print leaks( 2014). By 2017, 76 of associations reported phishing attacks, and phishing swindles on Amazon, cryptocurrency holdalls , and governments stressed its scale.
2010s – Global Expansion and High-Profile Attacks
The 2010s saw phishing attacks evolve into global, highly targeted campaigns. In 2011, RSA’s SecurID tokens were compromised via phishing. By 2013, retail giant Target lost 110 million records due to a subcontractor phishing breach. Fancy Bear, a Russian hacking group, conducted spear-phishing campaigns against NATO, the White House, and the Democratic National Committee (2016). Cloud services and social networks became top targets, with incidents like the iCloud celebrity photo leaks (2014). By 2017, 76% of organizations reported phishing attacks, and phishing scams on Amazon, cryptocurrency wallets, and governments highlighted its scale.
2020s – AI and Social Engineering Era

Phishing in the 2020s came more sophisticated with social engineering and AI- driven tools. The Twitter breach of July 2020 showed how bushwhackers used fake VPN spots and help desk impersonation to hack high- profile accounts, including those of Barack Obama and Elon Musk. bushwhackers decreasingly reckoned on Phishing- as-a-Service( PhaaS) platforms, making it easier for culprits to launch realistic juggernauts.
By themid-2020s, phishing reached record situations. According to APWG, more than 1 million phishing attacks were reported in the first quarter of 2025 alone, with over 3.7 billion phishing URLs detected globally. AI- generated phishing emails grew by 1,200 since 2022, and 82 of phishing juggernauts in 2025 now involve AI. Attackers use deepfakes to impersonate CEOs, politicians, and family members, tricking victims into transferring finances or participating in nonpublic data. In 2024, the U.S. reported over 105,000 deepfake phishing cases, causing$ 200 million in daily losses, while India lost ₹ 938 crore to AI- powered phishing swindles in just five months of 2025.
Phishing also expanded to smishing (SMS attacks) and quishing (QR code attacks), with reports of over 4 million crushing incidents in 2025. Despite better awareness, phishing thrives because of human error: studies in 2025 show 43% of breaches occur due to distraction, followed by lack of training (41%) and fatigue (31%). However, companies with strong awareness programs reduce phishing risk by up to 86% within a year, showing that prevention is still possible.