Introduction
In moment’s digital age, technology plays a central part in our diurnal routines. We calculate it for shopping, literacy, working, managing plutocrats, and operating essential services similar to healthcare, energy, and transportation. Although this technological advancement has greatly bettered our lives, it has also introduced new pitfalls. One of the most dangerous and disruptive pitfalls is ransomware, a form of cybercrime that has come decreasingly current.
In the last decade, ransomware has evolved from a minor nuisance into a major global trouble. A wide range of associations — including hospitals, seminaries, large pots, and government agencies have fallen victim to cybercriminals who seize control of critical systems and demand payment to restore access. To more understand this issue, let’s explore what ransomware is, how it works, real- life exemplifications, and the measures that can be taken to defend against it.

What is Ransomware?
Ransomware is a type of vicious software( malware) that encrypts a victim’s lines or locks them out of their system. Once infected, the bushwhacker demands a rescue payment — generally in cryptocurrency similar to Bitcoin — in exchange for restoring access to the data or system.
The term “ ransomware ” comes from the combination of ransom( a demand for plutocrats to release commodities) and software.
How Ransomware Works
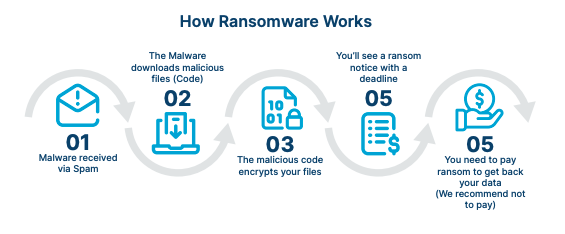
- Infection – The malware generally spreads through phishing emails, vicious attachments, infected websites, or software vulnerabilities.
- Encryption – Once outside, ransomware encrypts important lines, making them inapproachable to the stoner.
- Ransom Note – The bushwhacker displays a communication demanding payment in return for a decryption key.
- Payment & Recovery( Uncertain) – Victims may or may not get their data back indeed after paying the rescue, as cybercriminals frequently vanish after entering the plutocrat.
This system is effective because it preys on fear. Organizations frequently fear when they lose access to critical data, and some end up paying millions of bones just to renew normal operations
Common Types of Ransomware
- Crypto Ransomware Encrypts lines and demands payment for the decryption key.
- Locker Ransomware Locks users out of their bias fully.
- Scareware Pretends to be a licit security warning and demands payment.
- RaaS( Ransomware- as-a-Service) A model where cybercriminals rent ransomware tools to others for profit

Notable Ransomware Attacks
Several ransomware incidents have made captions in recent times, showing just how destructive these attacks can be.
- WannaCry( 2017) This was one of the most wide ransomware attacks in history. It infected further than 200,000 computers across 150 countries. Hospitals in the UK’s National Health Service were hit especially hard, with surgeries canceled and patient care disintegrated
- Petya/ NotPetya( 2017) Unlike WannaCry, which demanded reservations, NotPetya was further of a “ wiper. ” It spread encyclopedically, crippling companies and causing billions of bones in damages. Large pots like Maersk, a global shipping mammoth, were forced to shut down operations.
- Colonial Pipeline Attack( 2021) This attack targeted one of the largest energy channels in the United States. Operations were halted for days, leading to energy dearths across several countries. The incident stressed how ransomware can affect not just companies but entire communities and critical structure.
These examples remind us that ransomware is not just an IT issue, it’s a real- world problem with profitable, social, and indeed public security consequences.

Impact of Ransomware
The damage caused by ransomware goes far beyond paying money to criminals. Its effects can be long-lasting and devastating:
- Financial Loss – Victims frequently pay large totalities in rescue, plus spend plutocrats on recovery and during ages when their systems are not working.The cost to fix and rebuild damaged systems can be more advanced than the rescue quantum.
- Data Loss – In numerous situations,encrypted files can not be fully restored.Companies may lose important or nonpublic data that can not be replaced.
- Reputation Damage – guests may lose confidence in businesses that fail to secure their information.This can negatively affect the company’s character for a long time.
- Functional dislocation – Hospitals may delay treatments, manufacturers may stop product, and governments may break important services.These dislocations can have wide- ranging and significant consequences.
- Legal and Regulatory Penalties – Numerous countries have strict laws for guarding data. Businesses impacted by ransomware may face legal action, non supervisory scrutiny, or heavy forfeitures if they fail to adequately guard client information.
Why Ransomware Keeps Growing
Ransomware has come wide because it offers culprits a largely profitable occasion. Unlike traditional forms of theft, cybercriminals can launch attacks from anywhere encyclopedically without demanding to be physically present. They frequently use cryptocurrency as a accessible and anonymous system to admit payments.
In addition, bushwhackers are continuously perfecting their ways.
They employ artificial intelligence to produce realistic phishing emails and take advantage of zero- day vulnerabilities, which are security sins that inventors are not yet apprehensive of. The rise of Ransomware- as-a-Service has also made it easier for lower educated hackers to pierce advanced tools by hiring professional cybercriminal groups.
How to Protect Against Ransomware
- Regular Backups –Store duplicates of important data offline or in secure pall warehouses.
- Use Security Software – Keep antivirus and firewalls streamlined.
- Hand mindfulness – Train staff to fete phishing attempts.
- Patch Systems – Regularly update operating systems and operations to fix vulnerabilities.
- Zero Trust Approach – Limit access warrants and cover network exertion.
Should Victims Pay the Ransom?
This is one of the most batted questions in cybersecurity. Some associations choose to pay because the cost of time-out is indeed more advanced than the rescue. Still, security experts explosively discourage this. Paying only encourages culprits to continue attacking, and there’s no guarantee that data will be restored.
Rather, the focus should be on for estallment, backup strategies, and strong security practices. Governments and law enforcement agencies worldwide also advise against paying preservations whenever possible.
Conclusion
Ransomware is one of the most serious cyber pitfalls in the ultramodern digital geography. As bushwhackers continue to evolve their styles, for estallment and mindfulness are the stylish defenses. individualities and associations must borrow strong cybersecurity practices to minimize the threat. Paying ransom should noway be the first result, as it energizes the growth of cybercrime.
No association or existence is fully safe, but by staying alert, backing up data, and using ultramodern security tools, we can each make it much harder for cybercriminals to succeed.