Introduction
When most people think about hacking, the image that comes to mind is a person codifying furiously into a computer, breaking firewalls, and exploiting lines of law. While that conception exists, the verity is that one of the most important and dangerous tools in a hacker’s magazine is not specialized at all — it’s cerebral. This is what we call social engineering.
Social engineering is the art of manipulating people into revealing nonpublic information, granting access, or taking conduct that compromises cybersecurity. Unlike traditional cyberattacks that calculate on law, malware, or brute- force attacks, social engineering preys on mortal geste , feelings, and trust. In other words, rather than playing machines, it hacks the people who use
Why Social Engineering Works
Social engineering does not work in just one way. bushwhackers use different strategies depending on their target and thing. Then are the most common forms
1. Phishing
Phishing is the widest type of social engineering. Bushwhackers shoot fraudulent emails or dispatches that look licit — like from your bank, plant, or indeed a friend. The thing is to trick you into clicking a vicious link, downloading malware, or entering your login details on a fake website.
A popular variant is shaft phishing, where the bushwhacker personalizes the communication to a specific person or company. For illustration, they may source your job part or a recent design to gain your trust.
2.Pretexting
Then, the bushwhacker creates a fabricated story( or “ rationale ”) to gain sensitive information. For example, someone might pretend to be an IT support technician asking for your word to “ fix an issue. ” Because the request sounds reasonable, numerous workers misbehave without questioning it.
3. Baiting
Baiting uses curiosity or rapacity to bait victims. Imagine changing a USB drive labeled “ nonpublic ” in your office parking lot.However, you might intentionally install malware, If you plug it into your computer. Also, online baiting might involve free movie downloads that intimately contain contagions.
4. Seeing( or Piggybacking)
This system exploits physical security. A bushwhacker follows a sanctioned person into a defined area by pretending to be a hand who “ forgot their ID card. ” Since most people do not want to appear rude, they hold the door open — intentionally letting in a meddler.
5. Quid Pro Quo
This attack promises commodities in exchange for information. For illustration, a scammer might call workers offering free software updates in return for login credentials. Victims believe they’re getting precious but are actually handing over access to criminals.
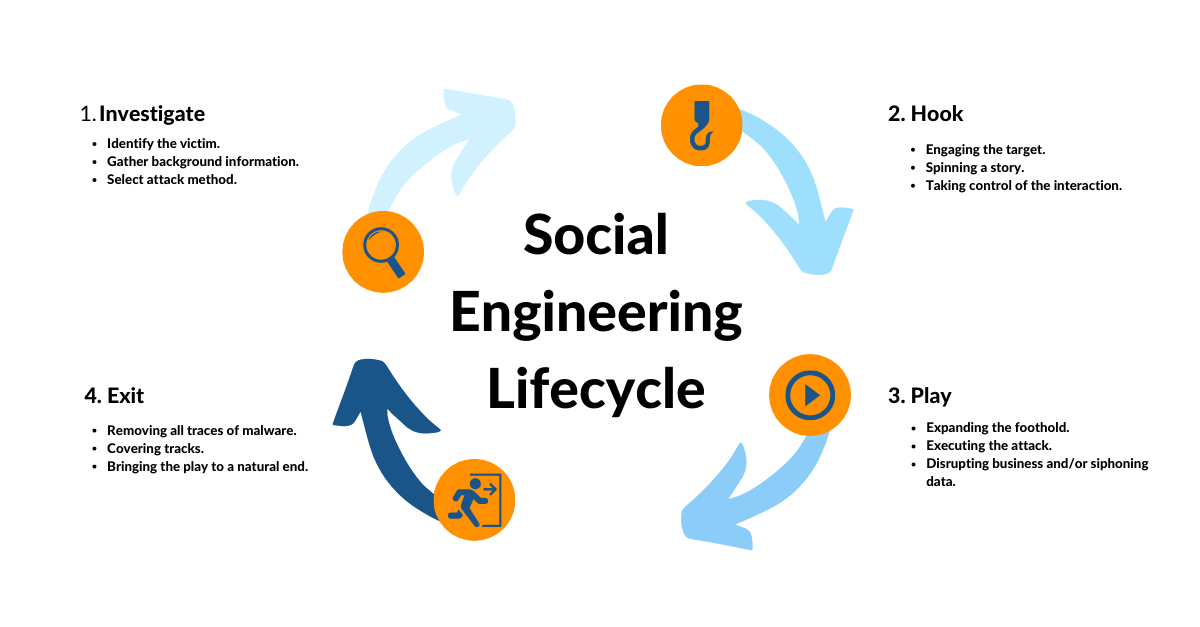
Real- Life exemplifications of Social Engineering
Some of the biggest cyber incidents in history started not with advanced malware, but with a simple mortal trick.
- The Twitter Bitcoin Scam( 2020) Hackers used social engineering to gain access to Twitter’s internal tools. They also commandeered the accounts of celebrities and companies to promote a Bitcoin fiddle . The loss was in the millions.
- RSA Breach( 2011) workers at RSA Security entered a dispatch with the subject line “ 2011 Reclamation Plan. ” It contained a vicious Excel train that gave hackers access to RSA’s systems — leading to a major breach of security.
- Google and Facebook fiddle( 2013 – 2015) A Lithuanian man tricked workers into transferring payments totaling over$ 100 million by impersonating a tackle supplier. He used nothing further than fake checks and dispatch correspondence.
These illustrations show that no matter how secure your firewalls and antivirus programs are, a single miss click or misplaced confidence can bring down a whole company.
The Human Cost of Social Engineering
Beyond fiscal losses, social engineering attacks can beget emotional and cerebral detriment. Victims frequently feel embarrassed for “ falling ” for a fiddle , which discourages them from reporting it. This silence only benefits bushwhackers, as they continue exploiting the same tricks on others.
For businesses, the consequences include
- Data breaches leading to reputational damage.
- Legal penalties for failing to cover client data.
- Loss of trust from guests and mates.
The most shocking part is that social engineering attacks do not bear high- end specialized chops. Anyone with enough tolerance and conclusive capability can essay them.
How to cover Against Social Engineering
The good news is that social engineering can be averted with the right blend of mindfulness, alert, and security practices. Then are some practical tips
1. Education and Training
The first line of defense is knowledge. Workers and individuals must be trained to fete suspicious emails, requests, and geste . Cybersecurity mindfulness sessions and dissembled phishing exercises can prepare people for real pitfalls.
2. Corroborate Before Trusting
No way to partake sensitive information unless you can corroborate the identity of the requester.However, hang up and call back using a sanctioned number, If someone calls claiming to be from your bank or IT platoon.
3. Slow Down
bushwhackers thrive on urgency — “ Do this in continently, or differently ” If a communication pressures you to act snappily, pause and double- check before responding.
4. Use Multi-Factor Authentication( MFA)
Indeed if your word is stolen, MFA adds a redundant sub caste of protection. A hacker who tricks you into giving away your login details may still be blocked if they do not have your phone or bio metric data.
5. Secure Physical Spaces
Associations should apply ID checks, caller logs, and programs to help tailgating. Indeed in the digital age, physical access is a critical security threat.
6. Keep Software streamlined
Social engineering attacks frequently aim to install malware. Regularly streamlining systems ensures vulnerabilities are renovated before they can be exploited.
The Future of Social Engineering
As technology advances, social engineering will only come more sophisticated. Artificial intelligence can now induce realistic phishing emails, clone voices, and indeed produce deepfake vids. Imagine receiving a call from someone who sounds exactly like your CEO, instructing you to transfer to a plutocrat. Without proper verification processes, seasoned professionals could fall victim.
On the wise side, AI is also being used to describe and block social engineering attempts. Dispatch pollutants, anomaly discovery systems, and behavioral analysis tools are getting smarter at relating suspicious patterns. But at the end of the day, technology alone is n’t enough — mortal mindfulness is irreplaceable.

Conclusion
Social engineering reminds us that the weakest link in cybersecurity is n’t the machine, it’s the person behind it. No matter how advanced our systems come, bushwhackers will always find ways to exploit mortal feelings like trust, fear, or curiosity.
The stylish defense is n’t just stronger firewalls or smarter software but smarter people. By staying alert, questioning unusual requests, and fostering a culture of cybersecurity mindfulness, we can make ourselves harder targets for social masterminds.After all, guarding information is n’t just about technology — it’s about people making better choices. And when people come harder to manipulate, social engineering loses its power.