Introduction
The digital world is growing more briskly than ever. From banking and shopping to healthcare and education, nearly every exertion moment takes place online. While technology has made our lives easier and further connected, it has also introduced new pitfalls.Cybercriminals are constantly coming up with fresh tricks to steal information, hack the accounts, and exploit security gaps.One of the easiest ways for bushwhackers to gain access is through weak or stolen watchwords. To deal with this weakness, cybersecurity experts recommend adding a redundant subcaste of protection called Two- Factor Authentication( 2FA).
Two- Factor Authentication is not a brand-new idea, but it has come decreasingly important in recent times as data breaches and playing attempts continue to rise. In this composition, we’ll explore what 2FA is, how it works, the different types available, along with its advantages, limitations, and why it has become a necessity in ultramodern cybersecurity.
Definition of Two-Factor Authentication

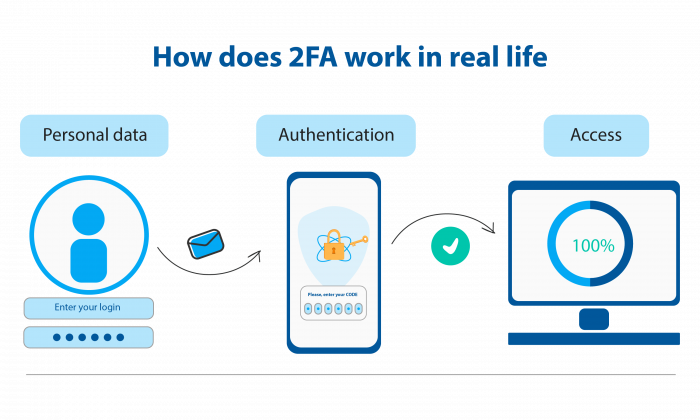
Two- Factor Authentication( 2FA) is a security medium that requires users to give two separate forms of verification before granting access to an account or system. Rather than counting solely on a password, it demands a redundant subcaste of evidence, making it much more delicate for hackers to break in.
Think of it like locking your house with two different types of locks — a crucial and a fingerprint scanner. Indeed if a pincher ever manages to steal your key, they would still fail to open the door without the alternate verification.
In simple terms, 2FA makes sure that the person logging in is the real account proprietor and not an pretender.
How 2FA Works
Two- Factor Authentication( 2FA) is built on the concept of using two of the three types of authentication factors listed below
- commodity you know-This includes a word, a particular Identification Number( Leg), or the answer to a security question.
- commodity you have- This could be a mobile phone, a tackle commemorative, or a one- time word( OTP)
- commodity you’re- This involves biometric data similar as a point, facial checkup, or voice recognition.
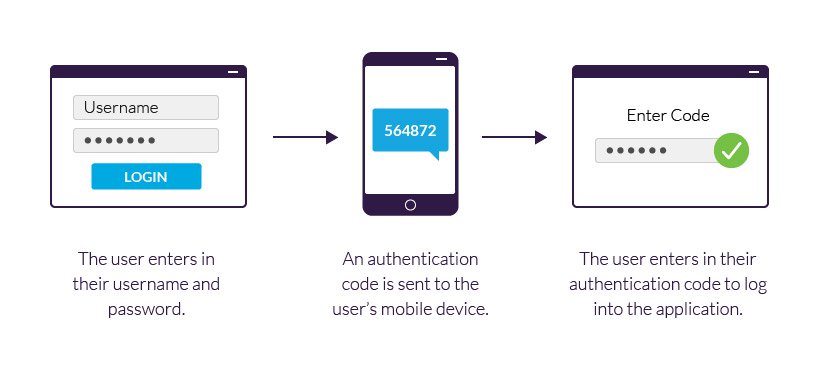
For illustration, if you want to log into your dispatch account, you first enter your username and word( commodity you know).Right after, you enter an OTP on your mobile phone( commodity you have). You need to input this law to finish the login process. This system ensures that indeed if someone steals your word, they still can not pierce your account without the alternate factor.
Types of Two-Factor Authentication
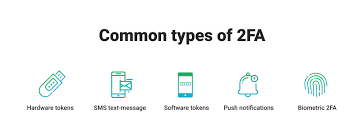
Over the years, several methods of 2FA have been developed. Some of the most common include:
1. SMS and Email Codes
One of the earliest and simplest forms of 2FA.After entering a word, the stoner receives a law via SMS or dispatch, which must be entered to confirm identity. Although accessible, this system is less secure due to SIM- switching attacks.
2. Authenticator Apps
Applications similar to Google Authenticator, Microsoft Authenticator, and Authy induce time- grounded one- time watchwords( TOTP). These canons change every 30 seconds, making them delicate for bushwhackers to prognosticate.
3. Push Notifications
Some services shoot an announcement to the stoner’s phone, asking them to authorize or deny the login attempt. This system is quick and more secure than SMS.
4. Biometric Authentication
Biometric identifiers similar as fingerprints, facial recognition, retina reviews, or voice patterns are decreasingly used as the alternate authentication factor. Since these are unique to each person, they give a strong defense.
5. Hardware Tokens
Physical devices such as YubiKeys or smart cards are used to generate a verification code or to be connected to a computer for authentication. These methods are highly secure but can be inconvenient because the device must be carried.
6. Email Links
Some platforms send a verification link to the user’s registered email address. The user needs to click on the link to confirm their login.
Importance of Two-Factor Authentication
The importance of two-factor authentication cannot be ignored in today’s digital environment. Here’s why it is essential:
- Protects Against Stolen Passwords:Passwords are often leaked in data breaches. With 2FA, even leaked credentials are useless without the second factor.
- Reduces Identity Theft:bushwhackers face further walls before penetrating particular or fiscal data.
- Secures Online Transactions: Banking ande-commerce heavily calculate on 2FA to secure plutocrat transfers.
- Builds Trust in Digital Platforms: users feel safer when platforms offer enhanced protection.
- Compliance with Regulations: numerous associations and governments bear businesses to apply 2FA for security compliance.
Advantages of Two-Factor Authentication

- Enhanced Security –provides a stronger hedge against hacking.
- Easy to Implement – numerous services like Google, Facebook, and banks formerly offered in 2FA.
- Cross-Platform Usage – workshop across multiple platforms, including dispatch, social media, and banking.
- Low Cost –atmost 2FA styles( apps, SMS) are free or affordable.
- Peace of Mind –users feel confident that their sensitive accounts are well defended.
Limitations of Two-Factor Authentication
While 2FA is effective, it is not completely foolproof. Some limitations include:
- Inconvenience: users may find it time- consuming to corroborate themselves every time.
- Device Dependency:If a stoner loses their phone or tackles commemorative, logging in becomes delicate.
- Vulnerable Methods: SMS- grounded 2FA can be interdicted via SIM- switching or phishing.
- Biometric Concerns:Biometric data, formerly stolen, can not be changed like a word.
- Phishing Attacks:Advanced phishing ways can occasionally trick druggies into revealing both factors.
Best Practices for Using Two-Factor-Authentication-2FA
For stronger protection, follow these stylish practices when using 2FA
- Always enable Two- Factor Authentication( 2FA) especially on critical accounts similar as dispatch, social media, and online banking.
- Prefer Authenticator Apps They’re more secure than SMS- grounded canons.
- Use Backup Codes Store recovery canons safely in case you lose access to your device.
- Update Security Settings Regularly review account security settings to stay streamlined.
- Be apprehensive of Phishing Never enter canons or authorize logins if you did not initiate them.

Real-World Examples of two-factor-authentication-2fa in Action

- Banking Banks frequently bear OTPs or biometrics for plutocrat transfers.
- Social Media Platforms like Facebook, Instagram, and Twitter offer 2FA to cover stoner accounts.
- Email Services Gmail and Outlook encourage 2FA to cover against unauthorized access.
- Commercial Networks numerous companies apply 2FA to secure hand logins and sensitive data.
- E-commerce Websites like Amazon and Flipkart use 2FA for safe purchases.
The Future of Two-Factor Authentication
With cyberattacks getting more sophisticated, the future of 2FA is evolving. Biometrics, AI- driven security, and passwordless authentication are anticipated to play a bigger part. Rather than counting solely on passwords, the world is moving toward multi-factor and adaptive authentication, where security adjusts dynamically based on user behavior .

For illustration, if you log in from your usual device and position, you may not be asked for 2FA. But if you log in from a new country, fresh verification may be needed. This approach enhances both security and convenience.
Conclusion
Two- Factor Authentication( 2FA) is one of the most effective ways to cover digital accounts from unauthorized access. By taking druggies to corroborate their identity through two different factors, it adds a strong defense subcaste against word theft, phishing, and identity fraud.
Although it may have some limitations, the advantages of 2FA far outweigh the downsides. In an age where cybercrime is growing fleetly, enabling 2FA is no longer an option but a necessity. Whether for particular use or business protection, 2FA ensures that sensitive information stays safe from vicious hands.
By espousing the 2FA moment, individualities and associations can take a significant step toward erecting a safer digital future.